I am currently pursuing my OSCP, but every now and then I like to take a break and mess with my homelab or take a look at some challenges. Yesterday on a slack I participate on, someone posted a link to a BSidesSF CTF that was ongoing with their account information in case anyone wanted to join in on the fun. I completed three challenges that didn’t seem too tough and wouldn’t take up too much of my time. Here are the write-ups for them.
Zippy
There’s several pcap files where you need to read the flag somehow. One of them is called zippy.pcap.

At first look we can see it’s all TCP traffic.
Going to Statistics > Conversations:

Following the stream for the first conversation:

Password is already there for when we need to use it, easy day. Now let’s take a look at the other TCP stream:
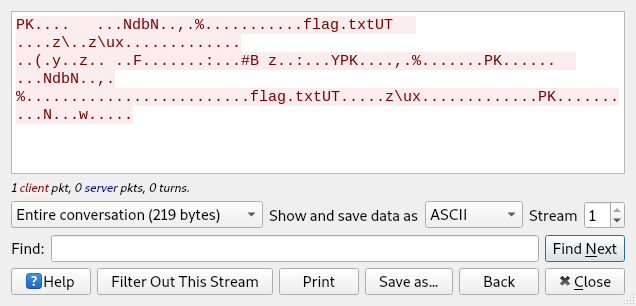
We can see the contents of this stream show “flag.txt”, so we can assume that we will probably extract the flag file from here. So let’s “Show and save data as” Raw:

I saved the file as “zippy.file”, and then used the command “file zippy.file” to confirm my suspicion that it is a zip file.

And since we already know the password to be “supercomplexpassword” we will use that to extract the flag.
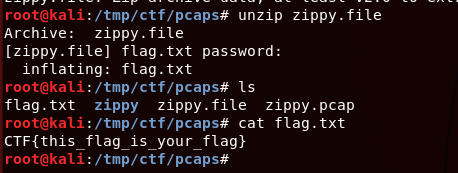
Got the flag!
Kookie
For this challenge, you just need to login as admin for the flag.
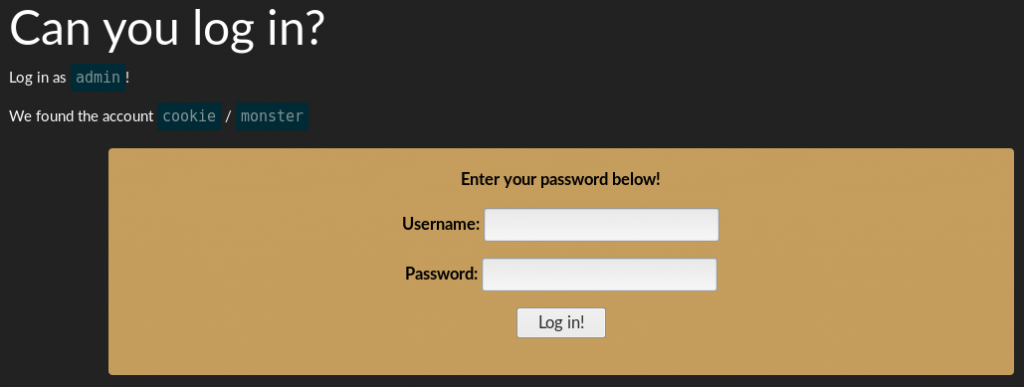
I initially thought the difficulty of this one would be harder than it really is. However, all you need to do is manipulate the session cookie as below:<br/>
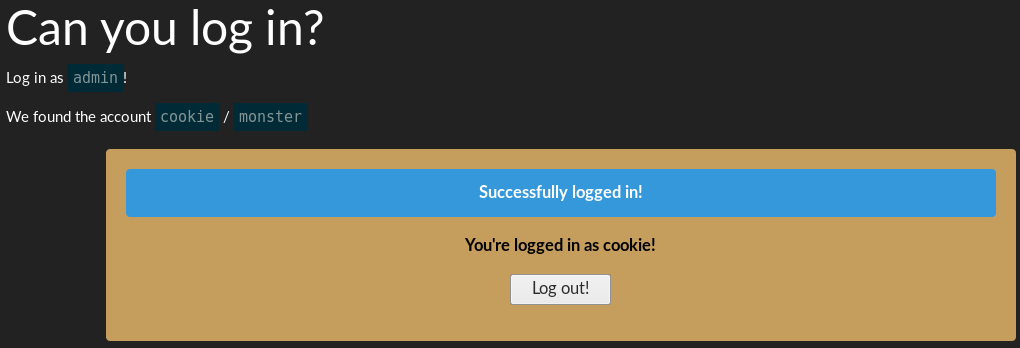
Open up developer tools / options:

Change cookie to admin:
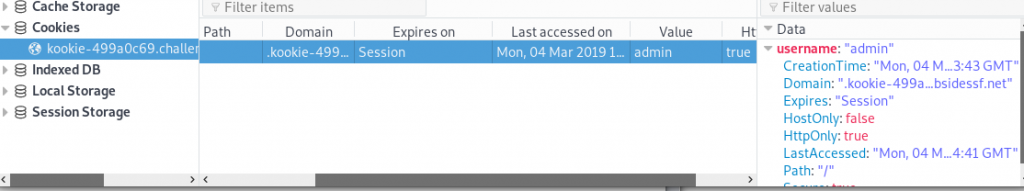
Refresh the page (F5):
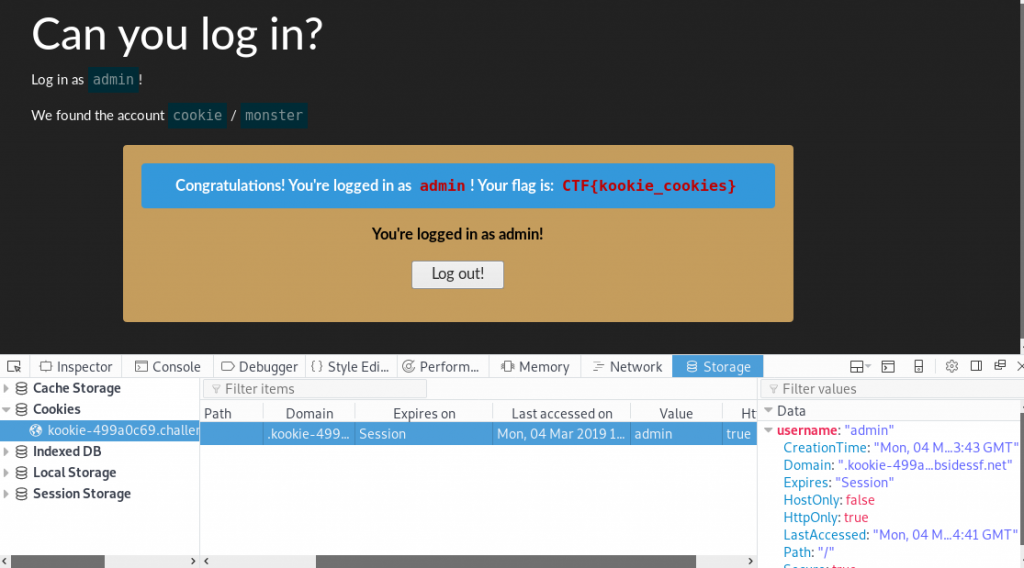
You have your flag! Easy stuff.
For the third challenge I did, I got the flag, but when submitting it to the BSidesSF CTF website it said it was incorrect. I’m inclined to believe I got it right, but once I finish the write-up for that one I’ll post it.