Here we will perform a token impersonation. There are a few ways an adversary can access tokens of elevated accounts, such as a domain administrator. For this walk-through, we will simply use Meterpreter.
Prerequisites:
- Domain controller with Active Directory setup.
- See this series, to set up your lab environment.
- Kali Linux
- Windows 10 VM, joined to a domain
- Meterpreter session established
- See this post, on gaining a meterpreter session.
First off, before we get into the attacking, it’s best we understand the type of attack / technique we are performing and what Access Tokens are. Per MITRE ATT&CK’s website, Access Tokens are:
Windows uses access tokens to determine the ownership of a running process.
https://attack.mitre.org/techniques/T1134/
And Token Manipulation / Theft / Impersonation is described as:
Adversaries may use access tokens to operate under a different user or system security context to perform actions and evade detection. An adversary can use built-in Windows API functions to copy access tokens from existing processes; this is known as token stealing. An adversary must already be in a privileged user context (i.e. administrator) to steal a token. However, adversaries commonly use token stealing to elevate their security context from the administrator level to the SYSTEM level. An adversary can use a token to authenticate to a remote system as the account for that token if the account has appropriate permissions on the remote system.
https://attack.mitre.org/techniques/T1134/
So now we know there are tokens within Windows that we can attempt to manipulate or steal to run commands as that user. The implications of this technique are pretty severe. It is entirely possible for an adversary to obtain SYSTEM level access with this technique, as well as Domain Administrator access, which is what we will see in this case.
Load Incognito
First off, we’ll take a look at what user is running in our meterpreter session. Then we’ll check out some modules we can load within meterpreter. We will use “load incognito”, and then check out some commands we can use within incognito.

Luckily, we’re running as SYSTEM, so everything should run smoothly. Type in “help” in your meterpreter command line. This will output a bunch of information, but right now we care about what is at the bottom of the output. Meterpreter will load the commands of the latest module that you loaded.

In the above image, impersonate_token is highlighted, but we will also use list_tokens to see what we can impersonate.

Delegate Tokens vs. Impersonation Tokens
Okay before we get ahead of ourselves, it’s good to know the difference between these two types of tokens. Because knowledge is power, and we aren’t going to fire off commands and attacks without first knowing what is going on at least at a high-level.
Delegate tokens are created for ‘interactive’ logons, such as logging into the machine or connecting to it via Remote Desktop. Impersonate tokens are for ‘non-interactive’ sessions, such as attaching a network drive or a domain logon script.
https://www.offensive-security.com/metasploit-unleashed/fun-incognito/
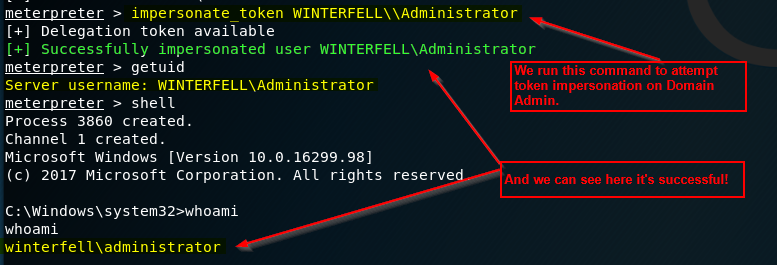
Impersonating Domain Admin token
As we can see in the above picture, there are several Delegation Tokens available when using “list_tokens -u”. See anything interesting? WINTERFELL\Administrator. Our domain admin’s token can be impersonated. Let’s give it a shot and see if it works.

And just like that it worked. We are now impersonating a domain administrator account. As mentioned earlier, the implications of this could be very bad. For example, being able to run net commands. Fortunately, I believe net commands for domain administration are disabled by default.

So there we have it. We can impersonate various accounts that are on our Windows lab environment. If you found yourself unable to perform this, or you enjoyed the content, feel free to leave a comment below or reach out to me on LinkedIn or at communities I am a part of (VetSec, The Cyber Mentor Discord).