Part I: Part I: Requirements / Installing Operating Systems
Part II: Part II: Setting up Active Directory
Part III: Part III: Joining Windows 10 to Domain, Mapping Shared Folder, & Quick Kali Configuration
Part IV: Part IV: Attacking
This is it! The final post of the series. We will not conduct our attack and gain Jon Snow’s hash. He knows nothing about creating strong passwords.
The Attack:
Get on Kali and locate Responder, the tool we’ll be using.


After starting Responder, in a separate terminal, get the IP Address of your Kali machine by typing “ifconfig”. Then go back onto the Windows 10 machine and paste this IP Address into file explorer’s path bar.

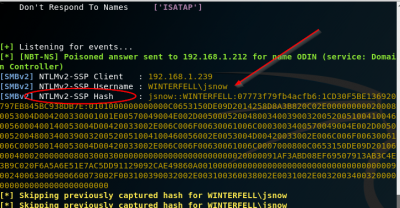
A pop-up will come up asking to login, but you don’t need to do anything here, you can click out. Go back onto your Kali machine and check to see if you caught Jon’s hash.

Awesome! We have the hash. Now we’re going to attempt to crack it using hashcat.





Copy the hash, go to a different directory (like root directory) by typing in “cd /”. Type in the terminal gedit and paste the hash into the editor. Hit save and close out. When cracking passwords, we need to use a program to do this along with a wordlist. The program we’re using is hashcat, but you could also use John the Ripper. A popular wordlist that should be built into Kali is “rockyou.txt”. You may need to extract rockyou.txt as its compressed.
Type in “locate rockyou.txt” and then unzip it with “gunzip /usr/share/wordlists/rockyou.txt.gz && cp /usr/share/wordlists/rockyou.txt .” This will unzip it and then copy it into the current directory you’re working out of.
Then we’ll start hashcat by typing in “hashcat -m 5600 hash.txt rockyou.txt –force”. –force is just added for good measures because we’re working out of a VM, and hashcat may be a bit fussy here. Hashcat should then be able to crack the password if it’s pretty weak.
And that is it! We set up an Active Directory server along with a Windows 10 machine, Kali Linux, and were able to successfully execute an LLMNR poisoning attack and intercept a hash, then crack it to gain credentials. I hope you enjoyed this write up. If you have any questions, feel free to reach out to me.