Hello all, this is going to be a two part series on Mimikatz and its powerful uses. First and foremost, if you haven’t set up an active directory lab environment yet, please do so by visiting this link –> https://mattschmidt.net/2019/05/10/llmnr-poisoning-part-i-requirements-installing-operating-systems/ and follow Part I and II of that series.
Note: This series is derived from TheCyberMentor (Heath Adams) in his paid Udemy course. Because of that, I greatly encourage everyone to purchase this course so you can have actual video and audio explanation of this tool, as well as have access to countless other amazing Penetration Testing topics that I don’t have the time to cover in written tutorials.
Twitter: https://twitter.com/thecybermentor
LinkedIn: https://www.linkedin.com/in/heathadams/
YouTube: YouTube – The Cyber Mentor
Udemy Course: Purchase here
The first part of this series will cover a quick overview of Mimikatz, loading it on a machine, and some quick uses of it.
Loading Mimikatz
You’ll need to load mimikatz on the machine you plan on dumping credentials for. Best (or worst?) case scenario is you’re on a Domain Controller. So for the following examples, we will be. Download mimikatz by going to the following github page:
https://github.com/gentilkiwi/mimikatz/releases
Make sure to grab the “mimikatz_trunk.zip” file and extract it on the target machine.


Now that you have mimikatz extracted on the machine, open up a Command Prompt as Administrator. So, click the windows icon, type “cmd” and right click and run as administrator.

Now change directories to the location which mimikatz is extracted, and run mimikatz.exe. Next, ensure you have the proper privileges (which you should if running as Administrator).
- cd C:\Users\Administrator\Desktop\mimikatz_trunk\x64
- mimikatz.exe
- privilege::debug
Here you’re looking for output which says “Privilege ’20’ OK”

So now we’ll try and dump some information from memory. It’s important to note that you’re not always going to have 100% success with every command we run, and we’ll show what this output looks like for some commands we try to run.
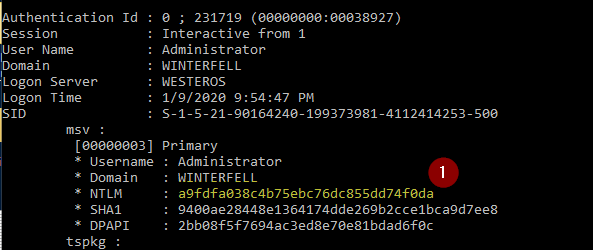
The first command we’ll run is “sekurlsa::logonpasswords”. What this does is show us the Computer, NTLM hash, as well as any users logged in since last reboot.

You can see above we have that NTLM hash that I mentioned, as well as the other information such as computer name and users. The output is generally longer and this is just a snippet, however we can take these NTLM hashes from this output and attempt to Pass the Hash with them. See this article regarding Passing the Hash: https://mattschmidt.net/2019/05/30/ad-hacking-pass-the-hash/
Additionally, we can take these hashes offline and try to crack them using my favorite hash cracking tool, Hashcat. So copy that Administrator hash, and save it. We’ll look into cracking these hashes in a little bit.
So let’s take a look at some other commands, which may or may not work. We’re going to try to dump the sam with “lsadump::sam” and “lsadump::sam /patch”.

No luck there! But this is all part of the process, and to show you what kind of error codes you may encounter.
The next command we’ll run is “lsadump::lsa /patch”. The LSA is the Local Security Authority which is a protected sub-system in Windows Authentication which authenticates and creates windows sessions to the local computer.

The type of information we see here are usernames and NTLM hashes. So now with this, we’ll try to take these hashes offline and try to crack them. Save these hashes where you saved the hash from the previous command where you have Hashcat saved.
Let’s try to just crack the first Administrator hash that we found, then all the other ones after. Run the command:
hashcat64.exe -m 1000 mimikatz-hash-example-ntlm.txt rockyou.txt
-m denotes the mode which we set as 1000. 1000 is the NTLM hash mode for hashcat. The mimikatz-hash-example-ntlm.txt file is where we have our hash stored, and rockyou.txt is the go-to wordlist when quickly trying to crack hashes.


As you can see above, the password was successfully discovered and the hash is cracked. You may be thinking, “But password123 is a really weak and stupid password, and no network administrator in their right mind would set such a weak password…” Well, you’d think that, but you’d be wrong.
I have personally ran many hashes through Hashcat and conducted a Password Database Audit of an international company since I’ve been working, and time and time again I see incredibly weak passwords for elevated accounts.
Okay, lets load up all those hashes from the lsadump.



And there you have it! We cracked more hashes and revealed more weak passwords, indicating to us that this company implements poor password policies and does not enforce strong password requirements. We did all of this very quickly with some commands from mimikatz, and running these hashes through Hashcat. It’s both cool and scary how quick we can compromise accounts with a combination of these tools.


