I purchased the WAPT coursework very shortly after becoming OSCP certified. But naturally, sometimes courses fall by the wayside as life gets in the way. The past two months I finally kicked it in high gear and started working harder on the course and am pleased to say that it Continue Reading
AD Hacking: Mimikatz Part I
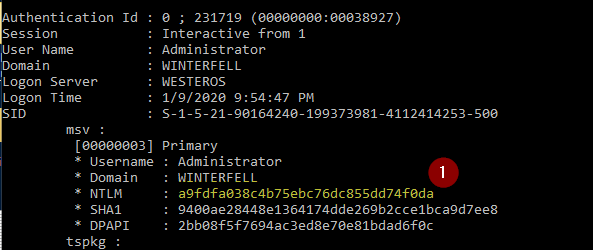
Hello all, this is going to be a two part series on Mimikatz and its powerful uses. First and foremost, if you haven’t set up an active directory lab environment yet, please do so by visiting this link –> https://mattschmidt.net/2019/05/10/llmnr-poisoning-part-i-requirements-installing-operating-systems/ and follow Part I and II of that series. Note: Continue Reading
New to Infosec? Some Humble Advice
At the time of me writing this post, I have been genuinely interested in Infosec for about 2 years now. Along the way, I’ve learned a great deal of knowledge that both excites and terrifies me. Every now and then, I have people coming to me asking for advice, mentorship, Continue Reading
Queen City Skiddies
For the past 6 months I’ve been hosting a Cybersecurity meetup in Charlotte, North Carolina primarily focusing on Offensive Security topics. I couldn’t be happier with how things have been running. We have had a steady group of people coming back time and time again and I am so proud Continue Reading
PWK/OSCP Helpful Tips & Resources
I’ve found myself giving people plenty of pointers and links that I think helped me out when I was doing the PWK coursework and the labs for OSCP. So because of that, I figured I’d actually collect everything in one spot and I can just refer anyone interested here. I’ll Continue Reading
eLearnSecurity WAPTv3 training begins
There is a saying in the Marine Corps that many Marines follow: “Complacency kills”. This essentially means that once you let your guard down and get comfortable, that’s when you’re at your most vulnerable. When you’re vulnerable, that’s when things can go sideways real quick. I think it is important Continue Reading
Getting Sponsored to go to BSidesLV, then tagging along to Defcon 27
Early on in May I applied to be sponsored (somewhat) by BSidesLV to go to the conference for free. BSides decided to invite five Veterans breaking into Cybersecurity who show promise and passion for the industry / lifestyle. All I had to do was pay for travel if selected. Well Continue Reading
AD Hacking: Pass The Hash
You may find yourself in a situation where you’ve gained some juicy hashes from a previous attack, but you’re unable to crack these hashes into clear-text. Well no worries, you can still look into passing the hash. Prerequisites: Hash obtained from previous attack. See any one of these posts for Continue Reading
AD Hacking: NTLM Relay Tutorial
A good URL with slides about NTLM relay can be found here. I recommend giving it a quick read and maybe watching a video to understand what is happening. Prerequisites: Domain controller with Active Directory setup. See this series, to set up your lab environment. Kali Linux Two (2) Windows Continue Reading
AD Hacking: Getting Meterpreter Session
Getting a Meterpreter session is always a wonderful thing. You can elevate privileges, dump hashes, clear windows logs, download/upload files, and more. Prerequisites: Domain controller with Active Directory setup. See this series, to set up your lab environment. Kali Linux Windows 10 VM, joined to a domain Setting your environment Continue Reading